About a month ago AppAssure released the first version of their backup software since being acquired by Dell. Dell AppAssure is one of the great sponsors on this blog so I figured hey, why not grab myself the trial version, install it, and share my experiences with my readers. I tried to take note of as many of the features as I could, but being in a limited nested workstation lab there was only so much I could do. So honestly, if you like what you see, I would go on over to AppAssure.com and get yourself your own free trial and give it a go. Also, although I only tested from within a VMware environment, AppAssure actually supports protecting machines across your complete infrastructure, being Hyper-V, VMware, and even physical machines.
INSTALLATION

First off is installation. AppAssure is installed on top of either Windows 7, Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012 (you must have a 64 bit OS, 8 GB of RAM and obviously some sort of storage.) The installation process was a breeze. There were a few prerequisites but as you can see the installer had the option to go ahead and install them for me. This is a small but great feature to have as there's nothing I hate more than searching around for prerequisites and updates. For the most part it was a 'Next->Next->Done' install.
CONFIGURATION
Once you have the AppAssure core installed you can access it by pointing your browser to http://HOSTNAME:8006/apprecovery/admin and logging in with your local administrator username and password. At this point you could click around and set everything up manually, but the 'Setup Core' button located near the top right of your screen will guide you through configuring mostly all of the parameters and functions that need to be setup in order to make AppAssure functional. The 'Setup Core' guides you through the following areas….
Display Name – This is simply the name you want displayed within your AppAssure core console – not a lot to talk about here.
Email Notifications – Here you can configure your SMTP settings, Email subject, and your to/from Email addresses. Another really small but very cool feature here is the ability to customize the actual message that the core is sending out. Using variables you can basically move information around in the message. As I said, a very small feature, but certainly a useful one.
Repository – This is the section where you define where you want your backups to go. Essentially you create a repository and then add one or more disk targets to it. The targets can be either direct attached storage or a cifs share somewhere on your network. By showing/hiding the details you can get very granular on how the repository stores its data by changing items such as bytes per sector, average bytes per record and whether or not you want Windows or AppAssure to handle the write caching.
Encryption – Another very useful feature especially for those with strict security standards. Here you have the ability to create an encryption key in order to fully encrypt (AES 256 bit) all of your backup data. This is not something that I see included with most backup software and it's certainly a nice to have feature.
BACKUPS
Now that all of the setup and configuration is done, we can get down into the core purpose for this application, and that's backing up your infrastructure. The 'Machines' tab is where we will spend most of our time for this section. This is where we will add and protect (this is the term AppAssure uses for backing up a client) our critical machines (AppAssure's term for a server, whether it be virtual or physical).
The first thing we need to do is deploy the AppAssure agents to a machine. The agents are used for many things but its main objectives are tracking changed blocks, performing quiescence of the applications, and handling all communication between the core and the client. This can be done by manually by installing the agents from the target machine, or you can simply use the 'Remote Deploy' wizard from the core. This will initiate the install of the agent and all of the required pre-requisites to the target machine. To do the latter, simply select 'Actions->Deploy Agent, provide the hostname and some credentials for your target machine and you are done. The status of this and almost all tasks can be monitored through the 'Events' tab.
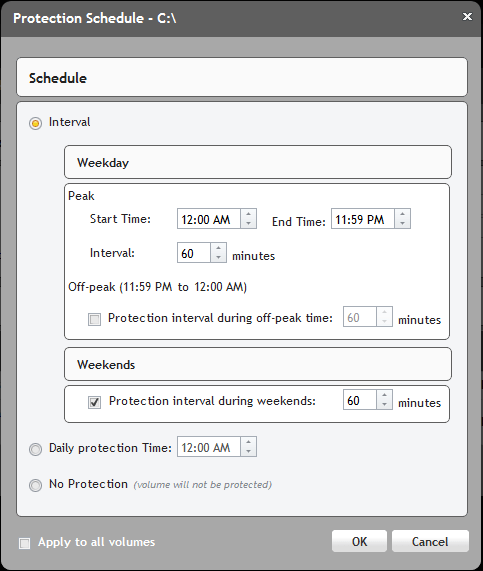
After the deploy has completed you still will not see the server listed on the Machine tab. We still need to add or protect the machine. To do so, select Actions->Protect Machine. In the dialog that appears we need to provide the hostname/ip and some credentials to connect to the machine. During this process you will also be able to edit what AppAssure calls their protection schedule. By default AppAssure will snapshot the machine every 60 minutes and perform a backup, however you can change these values during the addition of the machine by selecting 'Edit'. You can once again get very granular with how often you are performing the snapshots. You can specify different schedules for peak and non-peak times, as well as set different schedules for weekends as opposed to weekdays. Also, you can get as simple as saying one snapshot per day, or just disable protection all together.
Once the Protect Machine tasks have completed you should see your machine listed in the Machine tab. At this point you could just walk away as the protection schedule will kick in immediately and follow the parameters and policies that you set up during the wizard. Probably not the case however so as you can see below there are a few more tabs that we can go through dealing with this machine.
On the configuration tab there are several additional options that can be applied to your protected machine. First off the settings area allows you to change the display name and port/encryption information. Under Configuration->Events you can override the global email alert settings and configure alerts that are specific to this machine.
Under Retention Policy you can either use those core defaults that you set up earlier, or you can set up a customized retention policy for this machine. As you can see from the screenshot you are able to get very granular on how retention is handled and they have a very nice graphical representation of the retention information that you have selected. This is always a very confusing item for myself to configure and it's nice to have a visual to see how simple changes to your retention schedule affect the recovery points that are being saved.
Licensing, Protection Settings, and Transfer settings are again simply individual overrides from the global configuration. One huge note here (and I didn't have a chance to test all of this) is that if the target machine you are protecting is running SQL, Exchange, or SharePoint you will be given additional options such as the ability to truncate logs, etc.
From here you are basically good to go. You can let the protections settings take effect and start taking snapshots your machines. Or, you can immediately force a snapshot of your machine.
RESTORE
AppAssure handles restores in a few different ways.
 Mounting for a file-level restore
Mounting for a file-level restore















Replay 5 is a night and day improvement over 4. There are way fewer exceptions which require maintenance.
Thanks Eric…always nice to hear from someone who has used previous versions…
Is Dell offering 7x24x365 support? US based support? For me it’s a tossup between this and Backup Exec V-Ray
Yes Dell does offer 7x24x365 support for this product.
Have you tested a restore from MSSQL 2012 with Appassure V5 . ? Got issue with version Appassure v4 and MSSQL2012. I hope to test it soon in my lab.
Hi, What is offered in the trial version? is it time limited or resources limited?
14 day time limited
ty
so is this similar to Avamar from emc?
Has anyone tried it on Windows 2012 Server? Its not listed on supported OS yet, but as the writer did menion Windows Server 2012, I just want to know if it works or not.
Their post sales technical support sucks! Bought license and changed the in the core but still shows trial and will be expired in 72 hours. Called their support line, and get someone online and told me it is not supported by tech support. It belongs to licensing department and ask me to call back and select option for licensing (actually, there is no such option, call yourself at 866-459-6653). But I insist I have other issues like one of my server went down for over 12 hours but no alert or log shown in the event. He has no other and he has no way to check the status or my core, or see my log. So he ask me to email him the recovery log and recovery installation log which I did. And he emailed me back said it was escalated to level two technical support, and someone will call me ASAP. It never happened, so after 24 hours he said it was escalated, I called again. One of their tech support said: it was escalated and someone will call me. I said it never happened and it is going to expire in 12 hours now. Then she put me on hold for 10 min and come back to said she left notes to L2 support and someone will call me. When I ask, will someone call me before 5, she said no time frame. Then I ask to speak to a manager, and still holding now… over 5 min… will keep you posted!….
I have tried both v4 and v5 – and Kevin Lu is correct. There is absolutely no post sales support. The product is not predictable, backups can be faulty. I literally have to review all companies backups dailt to confirm they occurred. And when troubleshooting, not one person at technical support seem to have a clue what their custom error logs mean, although they were kind enough to send me a list of what errors I could see….seemed pointless since neither their support nor I could decipher what they meant.
I have had whole repositories of data vicariously disappear….of client data! and no explanation, no support, no call backs for days! At this point, I have spent literally hundreds of hours troubleshooting and figuring out the Dell Appassure product. I would not recommend this as a backup solution for any service provider.
Im sensing a pattern when it comes to support. I just used an nfr and never had any real issues, but never ran in full prod either. Thanks for the comment. Always good to have the real world experiences, be it good or bad. I hope you got things worked out
Another 10 mins waiting, and she came back told me the manager is not available…. so I ask if I can get the manager’s name, phone number or email address…. and I am on waiting again…….
Just hang up the phone, it was a two hours calls. Finally, one of their manager answered my call and transfer to their L2 support, and solved my problem. At least I can have a peaceful weekend without worrying my SAP production server.
Sounds like they may have some support process issues. Sorry to hear that. At the very least I’m happy it got resolved
I agree with Kevin Lu. Their tech support response time seems to be pretty bad. They don’t get that when your production systems go down that you NEED A CALL BACK. Been down all morning and still waiting on Dell to return a call.
I’ve had Appassure for a few years now. Prior to them being bought up by Dell, their great support was the reason we decided to go full blown Appassure. Now that Dell has acquired them I wait 2 weeks for a call back once my ticket has been escalated to “Tier 2”. My current issue I waited 3 weeks, and then got an email back which did me no good to fix the issue (which 5 weeks later still isn’t working and I still have not received a call back from them). Their virtual standby option has issues and I cannot get anyone to help me with it. Their technical support SUCKS!!! I’m with whoever said it below, should of bought Veeam!
No doubt this is a recurring topic in the comments. Hopefully everything gets ironed out
Support has added 50 plus people to address the extreme growth that Dell/AppAssure has had in the past few months. They are averaging less than a day at this point for support responses and continuing to make it even less time. AppAssure is a Great solution to have in place… and now that the support is beefed up getting resolutions to any challenges has been addressed … It will continue to be monitored.
I have had Appassure 5 up and running with 25 clients and a replication
core for a year now. I personally spend 10-20 hours a month babysitting
the software. Fixing hiccups and re-creating corrupted repositories etc.
Support is a horrid mess full of low-knowledge reps. If you get a
level 1 or 2 tech, you will spend several hours to days going around in
circles trying to fix your issue. If you can manage to get a senior
engineer, your issue will be fixed within an hour or so.
Appassure 5 has GREAT potential. However, it is poorly executed and supported. I still feel like the software is in beta.